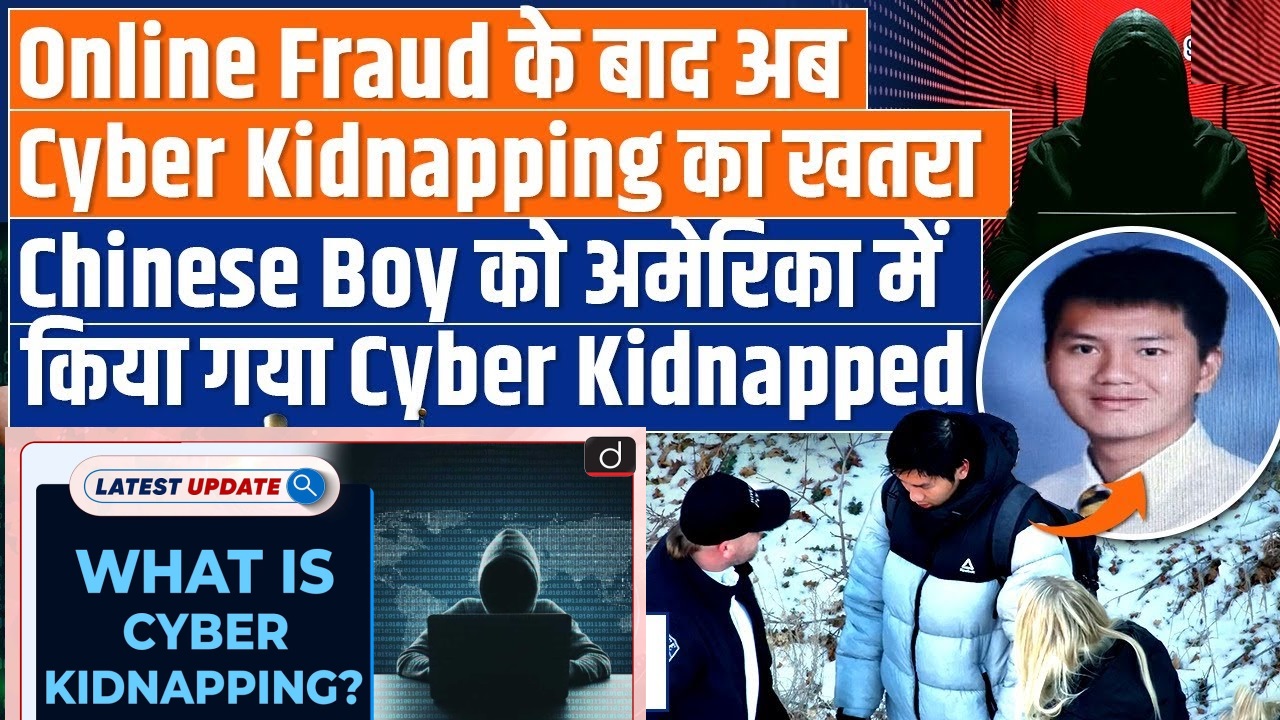
Cyber Kidnapping Scam: A Chinese Exchange Student’s $80,000 Ordeal
In the realm of online fraud and cyber threats, the story of a Cyber Kidnapping Scam $80,000 Ordeal Chinese exchange student has recently come to light, revealing the alarming rise of cyber kidnapping. This incident involves a high school student studying in the United States who fell victim to a cyber kidnapping scheme orchestrated by unknown perpetrators in China. The perpetrators not only abducted the student but also demanded a ransom from the student’s parents, who, in an unfortunate turn of events, deposited $80,000 into the kidnappers’ account.
The Cyber Kidnapping Scam Unveiled
Let’s delve into the details of this cyber kidnapping scam that targeted a Chinese exchange student studying in the US. Understanding the intricacies of the incident and learning how to safeguard oneself from such threats is crucial in today’s digital landscape.
The Exchange Student’s Ordeal
The victim, a Chinese exchange student attending high school in Utah, found himself at the center of this distressing incident. Hailing from Riverdale, a rural area in Utah, the 17-year-old student was reported missing on December 28. Shockingly, he was discovered hidden in a tent approximately 40 kilometers away from his school.
The Ransom Demand
The perpetrators, claiming to have kidnapped the student, terrified his parents in China. Fearful for their child’s safety, the parents, residing in China, succumbed to the kidnappers’ demands. They deposited $80,000 into the kidnappers’ account as a ransom to secure their child’s release.
Taking Action: How to Protect Yourself
In light of this alarming incident, it is essential for individuals preparing for competitive exams, like the UPSC, to stay vigilant against cyber threats. As we gear up to commence our foundation batch on January 8, focusing on Prelims, Mains, and Interview preparation, here’s how you can protect yourself.
Join Our Foundation Batch
Our comprehensive foundation batch covers Prelims, Mains, and Interview preparation, ensuring you receive all-encompassing guidance. Visit our website or utilize the code provided in the comment section for maximum discounts. The batch starts on January 8.
Specialized Programs for Success
For those solely concentrating on the 2024 Prelims, our Success in Prelims Plus program is launching on January 1. Don’t miss this opportunity to enhance your preparation. Visit my T.A page for more details and additional MCQ attempts.
Understanding Cyber Kidnapping
Before we conclude, let’s explore the concept of cyber kidnapping. Unlike traditional kidnapping, cyber kidnapping involves creating a facade of abduction to manipulate the victim. The perpetrators use convincing tactics to coerce the victim into compliance, often threatening harm to family members if their demands are not met.
In conclusion, the recent cyber kidnapping incident serves as a stark reminder of the evolving threats in our digital age. Staying informed and adopting cybersecurity measures is crucial to safeguarding oneself from such malicious schemes. The Riverdale Police Department’s collaboration with the FBI and insights from the Learn of a Disturbing Criminal Trend (L.D.C.T) through interactions highlights the need for awareness and preparedness in the face of cyber threats.
Understanding Cyber Kidnapping: A Comprehensive Guide
In the realm of cybersecurity, the menace of cyber kidnapping has become increasingly prevalent. This article delves into the latest updates on this alarming trend, with a recent incident involving a foreign exchange student in Utah, USA, as a focal point.
Unveiling the Cyber Kidnapping Phenomenon
The incident in question unfolded when a high school student, hailing from a foreign land, became ensnared in the web of cyber kidnapping. The perpetrators demanded a hefty sum of USD 80,000 from the student’s parents under the threat of harm. Fortunately, swift action resulted in the student’s rescue, albeit cold and frightened.
Cyber Kidnapping in the Digital Age
In the vast landscape of digital crimes, cyber kidnapping stands out as a sinister development alongside online scams and phishing schemes. This criminal trend involves scammers exploiting vulnerabilities in unsuspecting victims.
The Anatomy of Cyber Kidnapping
The process typically begins with scammers reaching out to their targets through calls or messages, creating a false narrative that a loved one has been kidnapped. Despite the fabricated peril, the victim remains physically unharmed. The aim is to coerce the victim into seclusion, compelling them to extort ransom money from their families.
Virtual Surveillance Tactics
Once the victim is isolated, cyber kidnappers employ video chat surveillance to monitor their every move. This not only intensifies the psychological pressure on the victim but also aids the criminals in executing their extortion plan.
Safeguarding Against Cyber Kidnapping
As the threat of cyber kidnapping looms large, adopting proactive measures becomes imperative. Here are some key strategies to ensure your online safety:
1. Enable Multi-Factor Authentication
Strengthen your online defenses by activating multi-factor authentication. This adds an extra layer of security, requiring more than just a password for access.
2. Utilize Security Apps
Leverage security applications to fortify the protection of your sensitive information. These apps play a crucial role in preventing unauthorized access.
3. Regularly Update Your Software
Stay one step ahead of cyber threats by keeping your computer software up to date. Automatic updates not only enhance functionality but also integrate essential malware protection.
4. Exercise Caution While Clicking
Exercise prudence when navigating the digital landscape. Be wary of popup ads and links received through emails from untrusted sources.
5. Strengthen Passwords
Avoid the convenience of using the same easy password across platforms. Opt for strong, unique passwords that act as robust barriers against potential hackers.
In conclusion, cyber kidnapping represents a grim reality in our increasingly interconnected world. By staying informed and implementing robust cybersecurity practices, individuals can fortify themselves against this evolving threat.